Attacks on websites and databases are increasing day by day rapidly. Among all of them sophisticated attacks are increased drastically, which affects small and medium sized companies. There are few features of these sophisticated attacks which involve high skilled attackers, also knowledge about the targets etc. So there must be some system to detect those attacks. A mechanism which is created to learn about the attackers’ method of attack and pattern and also used to get useful information about the intrusive activity is Honeypot.
What are Honeypots ?
One honeypot definition comes from the world of espionage or intelligence, where spies use a romantic relationship as a way to steal secrets are described as setting a ‘honey trap’ or ‘honeypot’. Often, an enemy spy is compromised by a honey trap and then forced to hand over everything he/she knows.
In computer security terms, a cyber honeypot works in a similar way, baiting a trap for hackers. It’s a sacrificial computer system that’s intended to attract cyberattacks, like a decoy. It mimics a target for hackers, and uses their intrusion attempts to gain information about cybercriminals and the way they are operating or to distract them from other targets.
Once an attacker falls into this trap, the honeypot allows administrators to obtain valuable data about the type of attacker, the activity he was attempting, and in many cases, even identify the attacker.
By monitoring traffic coming into the honeypot system, security analysts can assess:
- Where the cybercriminals are coming from
- Level of threat
- What modus operandi they are using
- What data or applications they are interested in
- How well the security measures are working to stop cyberattacks
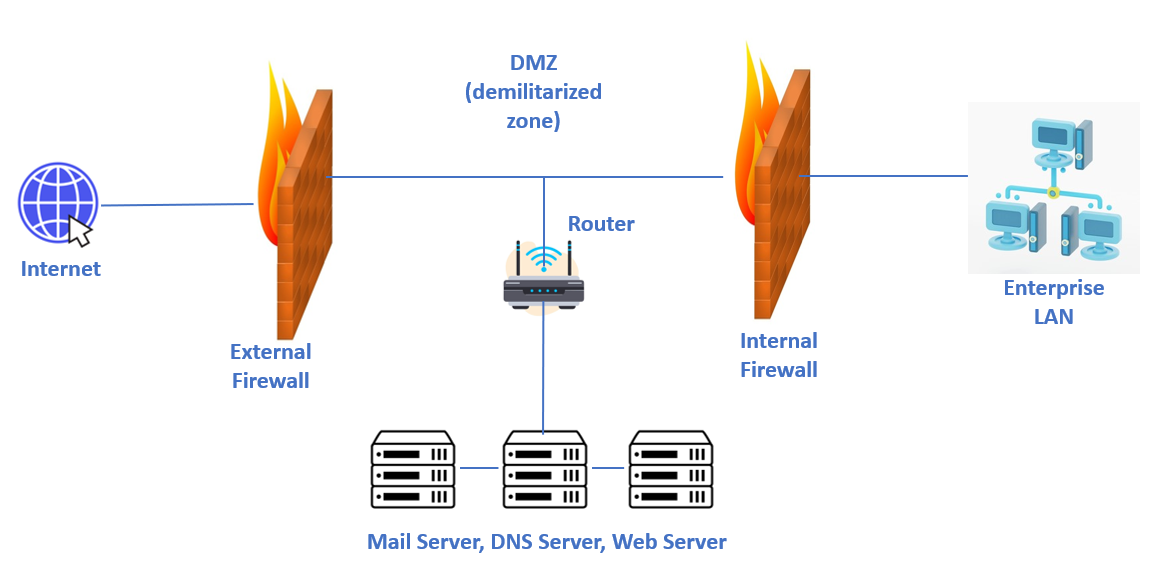
Honeypots Architecture
Honeypots may be single or a network of honeypots. Honeypots are commonly located at isolated DMZ segments behind Firewall. Honeypots often use hardened Operation systems where extra security measures are taken to minimize their exposure to threats. At the same time, it should appear to offer attackers exploitable vulnerabilities like SMB, SSH etc.
What is DMZ (Demilitarized zone) In computer networks, a DMZ, or demilitarized zone, is a physical or logical subnet that separates a local area network (LAN) from other untrusted networks -- usually, the public internet. Servers and resources in the DMZ are accessible from the internet, but the rest of the internal LAN remains unreachable.
Apart from this, honeypots can be deployed in order to consume the resources of the attacker or distract him from the valuable targets and slow him down, so that he wastes his time on the honeypot instead of attacking production systems.
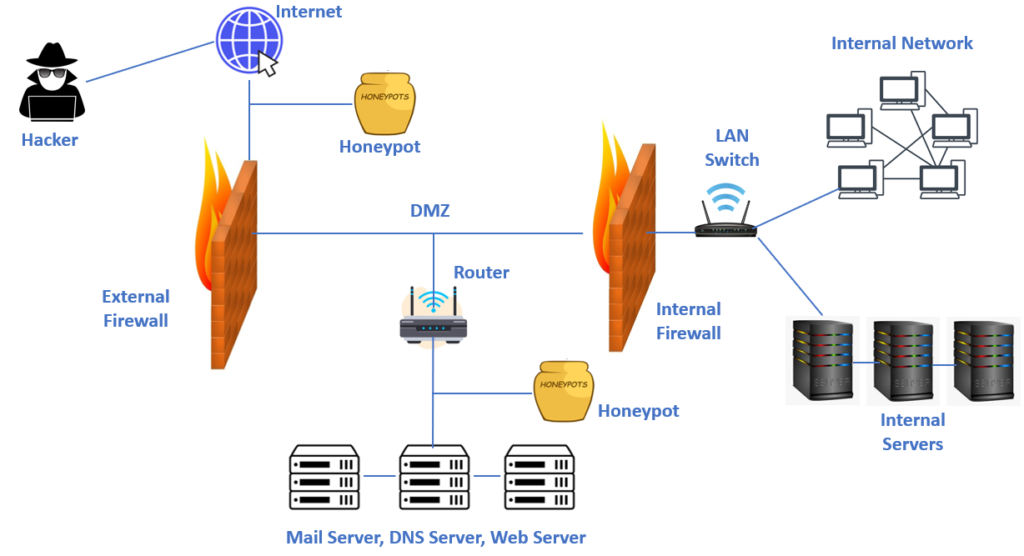
How does a honeypot work?
A honeypot is a trap system and these are often set up on a Virtual Machine or cloud server connected to a network, but isolated and strictly monitored by system and network teams. To help them get noticed by the bad guys, honeypots are designed to be intentionally vulnerable, with weaknesses an attacker will detect and try to exploit.
These weaknesses could be part of a security hole inside an application, or system vulnerabilities such as unnecessary open ports, outdated software versions, a weak password or an old unpatched kernel.
Once the attacker has found his vulnerable target, he’ll try to launch an attack and escalate privileges until he can gain certain control of the box or the application.
What most of them don’t know is that a honeypot administrator is watching each one of their steps carefully, collecting data from the attacker that will actually help to harden current security policies. The administrator can also report the incident to legal authorities immediately, which is what often happens with high-end corporate networks.
Most honeypots work as traps that distract attackers from critical data that is hosted on the actual networks. Another commonality is that almost all connection attempts to a honeypot can be treated as hostile, as there are few, if any, reasons that may motivate a legitimate user to connect with these types of systems.
While configuring the honeypot, one must be aware of the level of hacking difficulty he/she wish to expose to the attacker. If it’s too easy to hack, hacker will probably lose interest, or even realize they’re not dealing with a real production system.
On the other hand, if the system is too hardened, you’ll actually thwart any attacks and won’t be able to collect any data. So in terms of difficulty, luring an attacker with something between easy and hard is the best bet for simulating a real-life system.
A comprehensive source of honeypots can be found at the following URL:
https://github.com/paralax/awesome-honeypots
Honeypots Classification
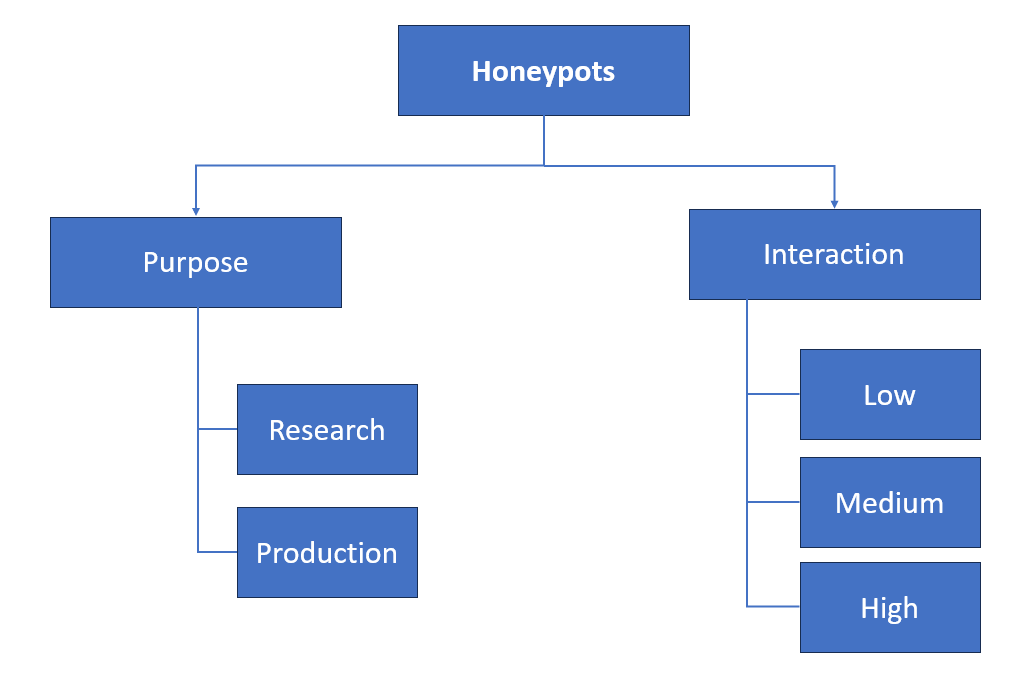
Honeypots can be classified based on the purpose as Research honeypot and Production honeypot.
Research honeypot: Research honeypots are basically used for learning new methods and tools of attacks. Research honeypots are used to gather intelligence on the general threats organizations may face, which gives the organization a better protection against those threats. Its main goal is to gain info about the way in which the attackers progress and performs lines of attacks. Research honeypots are complex to build, deploy and manage. They are basically used by organizations like universities, governments, the military and intelligence agencies to learn more about threats. Research honeypots provides a strong platform to study cyber-threats and forensic skills. [
Production honeypot: Production honeypots are simply aimed to protect the network. Production honeypots are easy to build and deploy, as they require very less functionalities. They protect the system by detecting attacks and giving alerts to administrators. It is typically used within an organization environment to protect the organization.
Also Honeypots can be classified based on the interaction as Low interaction, Medium interaction and high interaction honeypots.
Low-interaction honeypots present the hacker emulated services with a limited subset of the functionality they would expect from a server, with the intent of detecting sources of unauthorized activity. For example, the HTTP service on low-interaction honeypots would only support the commands needed to identify that there is an attempt.
Medium-interaction honeypots are slightly more sophisticated than low-interaction honeypots, but are less sophisticated than high-interaction honeypots. It provides the attacker with an illusion of the operating system so that more complex attacks can be logged and analyzed. Ex: Honeytrap: it dynamically creates port listeners based on TCP connection attempts extracted from a network interface, which allows the handling of some unknown attacks.
High-interaction honeypots imitate the activities of the real systems that host a variety of services. It let the hacker interact with the system as they would any regular operating system, with the goal of capturing the maximum amount of information on the attacker’s techniques. Any command or application an end-user would expect to be installed is available and generally, there is little to no restriction placed on what the hacker can do once he/she compromises the system.
In high interaction honeypot technology, by employing virtualization, multiple honeypots can be hosted on a single physical machine.
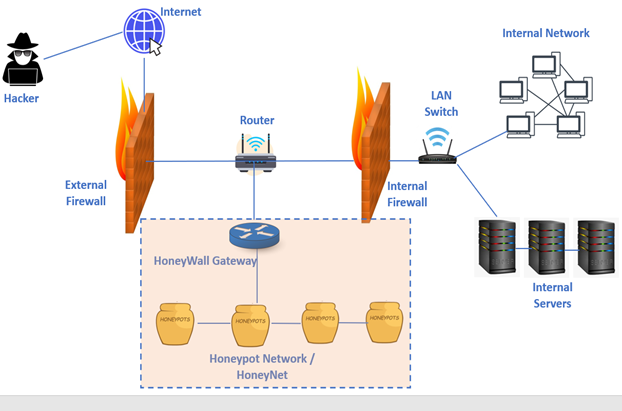
Honeynet: A Network of Honeypots
A honeynet is a decoy network that contains one or more honeypots. It looks like a real network and contains multiple systems but is hosted on one or only a few servers, each representing one environment. For example, a Windows honeypot machine, a Mac honeypot machine and a Linux honeypot machine.
A “honey wall” monitors the traffic going in and out of the network and directs it to the honeypot instances. You can inject vulnerabilities into a honeynet to make it easy for an attacker to access the trap.
Advantages of honeypot:
- Acts as a rich source of information and helps collect real-time data.
- Identifies malicious activity even if encryption is used.
- Wastes hackers’ time and resources.
- Improves security.
Disadvantages of Honeypots
Though there are several benefits of using a honeypot, doing so doesn’t come without risks. Some of them, like high-interaction honeypots, can be resource intensive and difficult to maintain.
- It may introduce additional risks into your environment. A compromised honeypot that’s not isolated effectively may be used launch an attack on the real network.
- It can only detect an intrusion when it is attacked directly. However, if an attacker identifies the honeypot for what it is, they can evade the system and infiltrate the network.
- Attackers may be able to fingerprint a honeypot (i.e. identify honeypots) based on certain specific characteristics such as misspelt error messages and so on. They can launch false attacks to distract administrators and while the organization chases these alerts, the attacker can focus on orchestrating a real attack.
Legal perspective on use of honeypots
There are 3 main aspects concerning the use of honeypots from a legal perspective:
- Entrapment
- Privacy
- Liability
Is it entrapment?
Honeypots are not a form of entrapment. For some reason, many people have this misconception that if they deploy honeypots, they can be prosecuted for entrapping the bad guys. Entrapment, by definition is “a law-enforcement officer’s or government agent’s inducement of a person to commit a crime, by means of fraud or undue persuasion, in an attempt to later bring a criminal prosecution against that person.
Does it violate privacy laws?
Privacy laws in the US may limit your right to capture data about an attacker, even when the attacker is breaking into your honeypot but the exemption under Service Provider Protection is key.
What this exemption means is that security technologies can collect information on people (and attackers), as long as that technology is being used to protect or secure your environment. In other words, these technologies are now exempt from privacy restrictions. For example, an IDS (Intrusion Detection System) sensor that is used for detection and captures network activity is doing so to detect (and thus enable organizations to respond to) unauthorized activity. Such a technology is most likely not considered a violation of privacy as the technology is being used to help protect the organization, so it falls under the exemption of Service Provider Protection. Honeypots that are used to protect an organization would fall under this exemption.
Does it expose us to liability?
Liability is not a criminal issue, but civil. Liability implies you could be sued if your honeypot is used to harm others. For example, if it is used to attack other systems or resources, the owners of those may sue. The argument being that if you had taken proper precautions to keep your systems secure, the attacker would not have been able to harm my systems, so you share the fault for any damage occurred to me during the attack. The issue of liability is one of risk. First, anytime you deploy a security technology (even one without an IP stack), that technology comes with risk. For example, there have been numerous vulnerabilities discovered in firewalls, IDS systems, and network sniffers. Honeypots are no different.
Note: This blog post is not legal advice and should not be used as such.